- By Richard Meagher
- Business & Technology
 Print
Print Now that you have successfully installed and reconnected your computers to the Internet using your new wireless network (and patting your 10 year old for reading you the directions in three languages), you are ready for the next step - protecting your network from intruders and attackers.
Unfortunately, many folks who have installed their own wired or wireless network often skip this last but very important step. The excitement of being untethered from a wall jack to browse the Internet, chat online and read e-mails while sitting in a more comfortable and convenient location in your home makes it easy to forget about taking these final steps to secure your network.
When we talk about protecting your wireless network from attacks, we are not talking about investing in a sophisticated signal scrambling system that could bring Q, James Bond’s gadget man, to tears. It is actually quite simple and a lot less dramatic, fortunately. So park the Aston Martin and come inside while we will cover this last but not least topic in setting up your wireless home network.
For Your Eyes Only
Why is this step so important? When you connect your computer to your cable modem, you have basically opened your electronic front door to everyone in the Internet. Unlike dialup services like AOL where you have to physically dial a connection using the phone anytime you want to browse the web, your cable or high speed broadband connection is always on, even when your computer is not running. If not protected, attackers can gain access to your computer within minutes of connecting to the Internet. Worse yet, some computers now have what is called Wake on LAN, which means that even if your computer is turned off while still connected to the cable modem, intruders can turn on your computer by sending a message to your computer’s network interface card and telling it to “wake-up” up your machine.
Intrusions like the ones above are likely if the computer is directly connected (wired) to a high speed cable modem and there is no router or home network installed. The first piece of information an intruder needs to break into your computer is an IP or Internet Protocol address. All computers or devices that connect to a network are assigned by the service provider a unique 32 bit address consisting of four numbers separated by periods with each number ranging from 0 to 255. One example of an IP address may look like 24.59.111.118. The address is assigned often dynamically by the broadband service provider but you can also get a static IP address assigned for business or commercial purposes.
To protect your computer from intrusion or attacks on the Internet, a router, like the ones we reviewed in the last installment of this series of articles, is recommended. Routers protect both wired and wireless networks by acting as a firewall. In wired networks, the router takes the dynamically assigned IP address from the broadband service and then assigns your computer and other computers in your home network different IP addresses not visible to computers outside your home network.
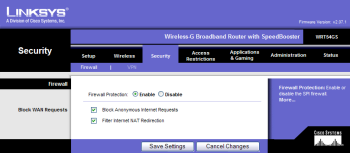
The router in effect hides your home network from the Internet. It does this by checking and blocking unauthorized requests from the Internet to gain access to your network and your computers connected to it. Once the router firewall is enabled, your wired home network is protected and your computers can hum along happily sending messages to each other and receiving only messages that the router believes is safe from the Internet. An example of enabling your router firewall using a Linksys router is shown below: (Note, all graphics represent a specific brand and model series so it may not reflect other brands or more recent models. Read manufacturer’s instructions provided on CD or in paper form) .
Wireless networks have a different kind of addressing that is actually a new hole hackers can easily find to access to your network. This type of addressing is referred to as SSID or Service Set Identifier. Unlike IP addresses, SSID addresses are broadcast to other wireless devices within the range of the wireless spectrum so others can find it and connect to it.
Here are two examples of how easy it can be to gain access to a wireless network or computer if not properly protected. Say I am enjoying a cup of roasted java beans at my favorite bookstore café and working on my latest cyber-sleuth novel. I am using a wireless modem with a paid subscription through a local cell service provider to connect to the Internet.
Meanwhile, another user comes in and takes a table nearby, turns on her laptop and after a few seconds (a very fast machine), looks for a network to log into and finds several network connections available. She unknowingly clicks on my computer’s SSID on the list and since I didn’t bother to properly set up the security settings, she finds herself browsing the Internet through my computer on my dime.
In another example, a student has a wireless network in his apartment shared by his roommates. He also has a high volume color laser printer with a wireless interface connected to the network, and a large network storage device (like a hard drive connected to the network).
One day, a neighbor who is familiar with the student decides to play a little prank and print an electronic illustrated copy of Tolstoy’s War and Peace on the color laser printer. He waits until the student and his roommates leave to go to a hockey game. He turns on his laptop to get to work and, like the young lady in the bookstore example, finds the student’s network name popping up on his screen. He locates the giant 6 gigabit Tolstoy file on his computer, copies it to the network storage device in the student’s apartment and issues the print command to the color laser printer. All this without having to set foot in his victim’s apartment. As for getting the printed copies – I’ll save that for my novel.
So how was all this possible? In both examples, the wired network and computers with wireless interface operate in what is commonly referred to as an open system authentication. This is usually the default setting when setting up a wireless network and obviously not a recommended setting.
The following steps occur when two devices use Open System Authentication:
1.Device A sends an authentication request to Device B.
2. Device B which acts as an access point authenticates Device A.
3. Device A associates with Device B, the access point, and joins the network.
It’s that simple!
----
----
v1i18




